DeepSeek restricts sign-ups amid ‘large-scale malicious attacks’
In an age where digital platforms often serve as lifelines for connection and expression,the security and integrity of these online spaces have never been more critical. recently, DeepSeek, a rising star in the realm of search technologies, found itself facing an unprecedented challenge—a wave of large-scale malicious attacks that compelled the company to pause new sign-ups. This precautionary measure, while aimed at protecting user data and maintaining service quality, raises crucial questions about the vulnerabilities that even the most innovative platforms can encounter. As the digital landscape continues to evolve, the need for robust security measures takes center stage, prompting a reevaluation of how companies can safeguard thier communities against an ever-changing threat environment. In this article, we will explore DeepSeek’s decision to restrict sign-ups, the nature of the attacks it has faced, and the broader implications for online safety in today’s interconnected world.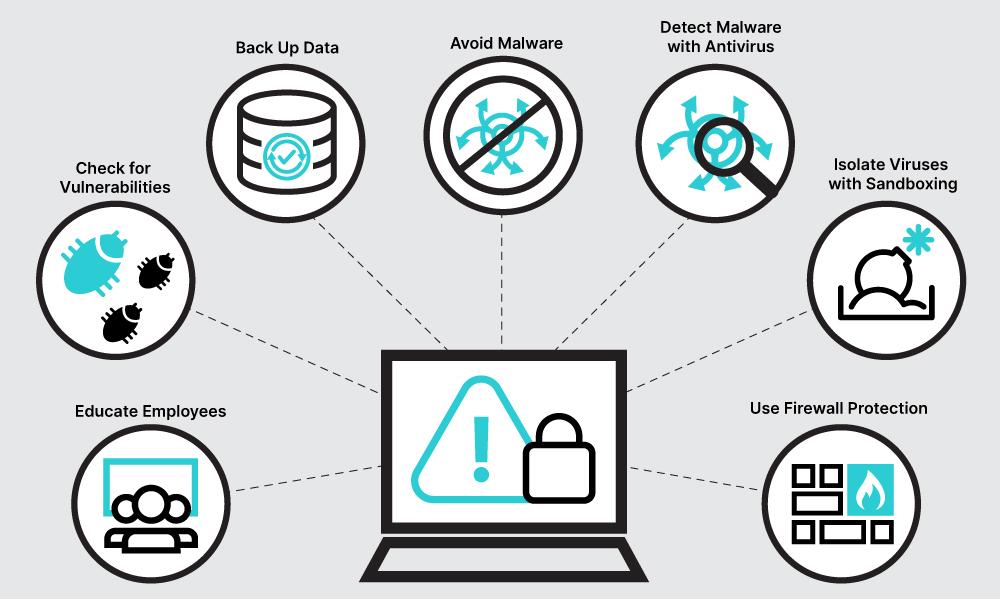
Understanding the Surge in Malicious Attacks on DeepSeek
The recent uptick in malicious attacks targeting DeepSeek has raised meaningful concerns among its user base and the cybersecurity community alike. As hackers deploy increasingly elegant techniques, several factors have contributed to this surge:
- Increased User Traffic: The platform has gained popularity, making it a more attractive target for cybercriminals.
- Data Sensitivity: With a wealth of valuable information, DeepSeek is a high-value target for those seeking monetary gain.
- Exploitable Vulnerabilities: As software evolves, new weaknesses may arise, providing entry points for malicious actors.
- Global cyber Trends: A general rise in cyberattacks worldwide has emboldened attackers to exploit perceived weaknesses across various platforms.
This escalation in threats has prompted DeepSeek to implement stricter sign-up protocols, ensuring user data integrity and platform security are prioritized.

Analyzing the Implications of Restricted Sign-Ups for Users
The recent decision by DeepSeek to limit sign-ups has sent ripples through its user base, raising concerns and questions about accessibility and security. While some applaud the move as a necesary measure against rampant cyber threats, it undeniably creates barriers for new users seeking to benefit from the platform. Key implications include:
- Increased Security: By controlling the influx of new accounts, the platform can better monitor and mitigate risks associated with malicious activities.
- User Trust: Current users may feel more secure knowing that the platform is taking a proactive stance against potential threats.
- Market Position: Restricting new sign-ups may enhance DeepSeek’s exclusivity, positioning it as a more secure option in a competitive landscape.
- Potential Loss of Revenue: With restricted access, the platform might experience a dip in user acquisition, impacting long-term growth projections.
Moreover, the platform’s decision could provoke a shift in user demographics, as potential users might seek alternative services, potentially leading to a fragmentation in the user experience within the sector.

Mitigating Risks: Best Practices for online Security
in an era where cyber threats are evolving at an unprecedented pace, organizations must adopt a proactive stance in safeguarding their digital assets. Deploying complete strategies can considerably reduce vulnerabilities while enhancing overall digital resilience. Consider implementing the following best practices:
- Regular software Updates: Ensure all software is updated to the latest versions to patch known vulnerabilities.
- Multi-Factor Authentication: Enhance security by requiring additional verification methods beyond just passwords.
- User Education: Conduct training sessions to raise awareness about phishing scams and social engineering tactics.
- Data Encryption: Utilize encryption for data at rest and in transit to protect sensitive information.
Additionally, maintaining a regular review of security protocols can definitely help identify and rectify potential weaknesses:
| security Measure | Frequency of Review |
|---|---|
| Software Updates | Monthly |
| Access Controls | Quarterly |
| Incident Response Plan | Bi-Annually |
By integrating these strategies, organizations can fortify their defenses against large-scale attacks, ensuring a more secure online environment for all users.

Future strategies for DeepSeek in Combatting Cyber Threats
as DeepSeek navigates the complexities of current cyber threats, adopting innovative strategies will be crucial for safeguarding its platform and users. The company plans to enhance its defences through the following initiatives:
- AI-Driven Threat Detection: Integrating advanced machine learning algorithms to identify and neutralize threats in real-time.
- User Education Programs: Implementing comprehensive training modules for users to recognize and report suspicious activities.
- Partnerships with Cybersecurity Firms: Collaborating with industry leaders to share intelligence and develop robust security protocols.
- Regular Security Audits: Conducting bi-annual assessments to ensure the integrity of existing security measures and identify potential vulnerabilities.
By focusing on these areas,DeepSeek aims to foster a resilient environment capable of adapting to the evolving landscape of cyber threats. Ensuring that both the platform and its users remain protected is paramount for continuing to build trust within the community.
The Conclusion
As DeepSeek navigates these turbulent waters, the decision to restrict sign-ups underscores their commitment to safeguarding user experience and data integrity. While these measures may temporarily limit access for new users, they signify a proactive approach to combat the rising tide of malicious activities online. In an era where digital security is paramount, DeepSeek’s actions remind us of the importance of vigilance in the face of threats. As the tech landscape evolves, it will be crucial for platforms and users alike to remain informed and resilient, ensuring the digital sphere can thrive free from the shadows of cyber malfeasance. Only time will tell how effectively DeepSeek can fortify its walls and eventually welcome a new wave of users while maintaining the sanctity of its service. For now, staying safe online is a collective duty—one that demands our attention as we all evolve with the technology that connects us.